We often observe applications bundled with ad-displaying programs to generate revenue for those products. These are not necessarily unethical, but some of them try to make easy money by deceiving users. McAfee categorizes such apps as potentially unwanted program (PUPs). Here’s a look at a recently discovered Russian-based campaign that is very well organized.
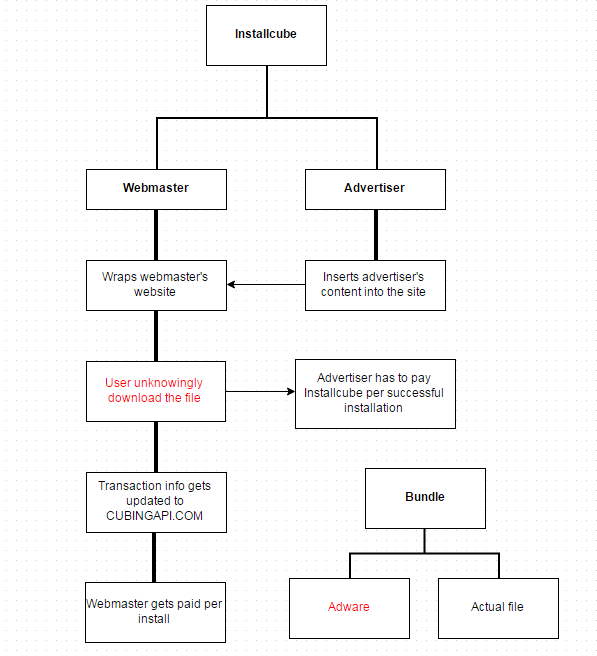
We can summarize the flow of campaign with this flowchart:
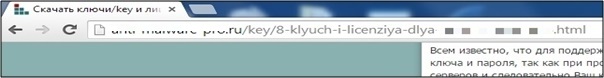
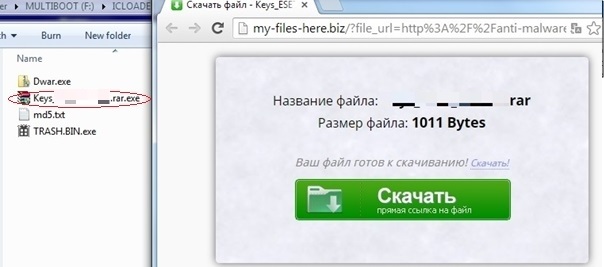
We came across one of the many sites that are part of this campaign. This site promises to give users pirated keys for various antimalware software so that they can use AV products for free.
Wrapped website.
Wrapped RAR file download button.
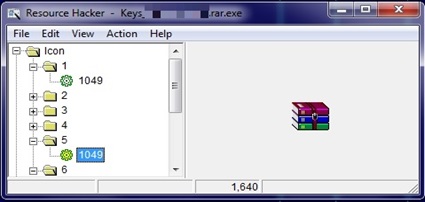
The keys are offered in a RAR file that is available on the site. However, we found this to be an adware executable with the name sample.rar.exe, which has a RAR icon to misguide users into thinking the file is an archive instead of an executable. One click by the user, and the adware is executed.
Icon resource of executable posing as a RAR file.
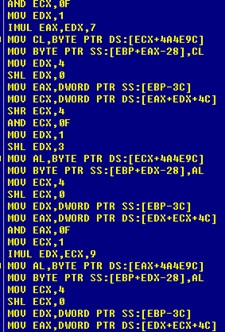
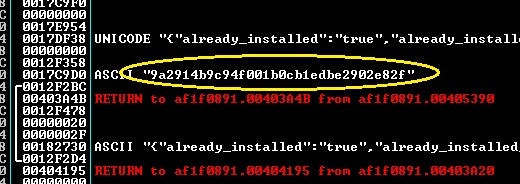
After executing, the sample first reports a confirmation to the back-end server of InstallCube (cubinapi.com) with a unique load ID. The load ID comes from an algorithm that generates a number from the composition of range 0-9 and a-f. Each character of the key is generated using a different algorithm.
Fragment of algorithm to generate the key.
Generated post key.
This unique count helps determine how far the ads spread and eventually is converted to cash.
After loading the execution stat, the executable opens a page in Internet Explorer that has a big green download button and small download link. If the button is clicked, it will lead to two possible downloads: Either a big file (10MB-20MB) or a small executable (less than 1.5MB), which is the ad-producing software. Refreshing the same link will lead to various files being downloaded.
Bundle download button.
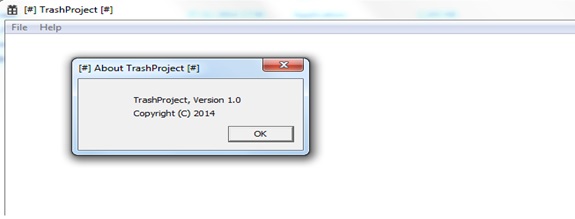
The big file is Trash.exe and pretty much justifies its name. This is a simple application made in Visual C++ and its only function is to display a dialogue reading “Trash Project, Version 1.0.” The likely use for such a big file is to create traffic to certain sites.
Trash.exe file.
In the following chart we can see the conversion of ads into cash:
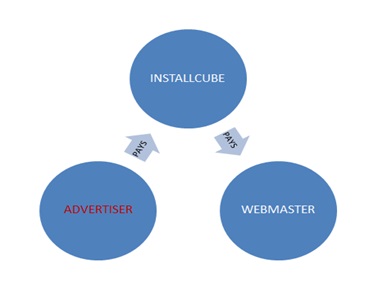
The money flow.
We tried to register our account on InstallCube, which promised us that our software would be wrapped in a packer and installed to a number of users. However, to start the campaign they demanded at least 2000 rubles.
Installcube demanding payment from advertisers.
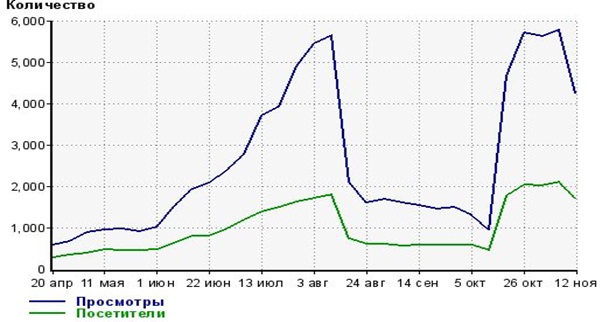
If the webmasters host only the deceptive adware and not useful files, traffic to their sites will decline because of unsatisfied customers. In this following chart we see this issue addressed by a webmaster, demonstrating the drop in traffic after the adware was hosted on his site.
Graph showing amount of views (blue) and visitors (green).
As a result, sites host the adware for a only short time, and periodically remove it so that the reputation of the site remains good. The adware executables on this site are also briefly hosted and are frequently replaced by useful files.
InstallCube is not the only organization profiting from this campaign. The webmasters who host misleading software are also making quick money by using InstallCube. In the following Russian blog we found a discussion among webmasters about how to use this software to make money.
Showing ads is not always bad behavior, but in this case two breaches make this campaign unethical. First is the deception of making an executable appear as an archive, and second there is no mention of the ads (such as an End User License Agreement). Users are given no options and become victims of the ad campaign as soon as they click the fake executable.
Such ads and force-fed bundled software are not malware, but they can annoy users and also take up a chunk of their bandwidth.
McAfee has blacklisted the InstallCube site and the back-end tracking service.
We also offer generic coverage of ad-producing executables as PUP-FSP, PUP-FRP, PUP-FQL, and PUP-FPA.